Understanding Digital Signatures and Hashing by MS Technology
Published: February 02, 2024
In the rapidly evolving landscape of digital communication and documentation, the traditional methods of signing and verifying documents are gradually giving way to more advanced and secure alternatives. One such game-changing innovation is the use of digital signatures in documents. In this blog post, we’ll delve into the world of digital signatures, exploring their significance, and the positive impact they can have on today’s world.
Power of Digital Signature
A digital signature is a cryptographic technique that ensures the authenticity and integrity of a digital document. Unlike a traditional ink signature, which can be easily forged or tampered with, a digital signature provides a unique fingerprint for a document, making it virtually impossible to alter without detection.
It uses a pair of cryptographic keys: a private key, known only to the signer, and a public key, available to anyone who wants to verify the signature. The private key is used to create the signature, while the public key is used to verify it. This robust system ensures that the signature is both unique to the signer and mathematically linked to the content of the document.
What is e-Signature?
An electronic signature, often abbreviated as e-signature or even eSignature, digital representation of a person’s intent to agree to or approve the contents of a document, transaction, record, or forms. E-signatures are commonly used in various industries to streamline and expedite the signing process, reducing the need for physical paperwork.
Digital Signature Vs e-Signature
A digital signature is a specific type of eSignature that relies on cryptographic techniques for enhanced security and is often associated with a higher level of legal recognition. E-Signatures, on the other hand, encompass a wider range of electronic methods for indicating consent or approval, and their legal standing may vary based on jurisdiction and specific circumstances. Digital signatures use a unique identifier, often based on a digital certificate, to verify the identity of the signer and ensure the integrity of the signed document. E-signatures are generally considered less secure than digital signatures, especially when they rely on less secure methods of verification.
While all digital signatures are electronic signatures, not all e-signatures are digital signatures. They have distinct differences in terms of their technology, security mechanisms, and legal implications.
- Technology:
- Digital Signature: A digital signature is a cryptographic technique that involves the use of a digital key pair (public and private keys). The private key is used to sign a document, and the corresponding public key is used to verify the signature. Digital signatures provide a higher level of security and integrity to the signed document.
- E-Signature: eSignature is a broader term that encompasses various electronic methods used to indicate a person’s intent to agree or approve a document. This can include simple electronic symbols, scanned images of handwritten signatures, or more advanced methods like digital signatures.
- Security:
- Digital Signature: Digital signatures rely on cryptographic algorithms and the security of key pairs to ensure the authenticity and integrity of the signed document. They provide a higher level of security and are often used for sensitive or legally binding transactions.
- E-Signature: While e-Signatures can offer security features, they may not be as robust as digital signatures. The security level can vary depending on the method used, and simpler e-Signatures may be more susceptible to forgery.
How hashing is used in Digital Signatures?
In the context of digital signatures, hash functions play a crucial role in ensuring the integrity and security of the signed data that involves several key steps:
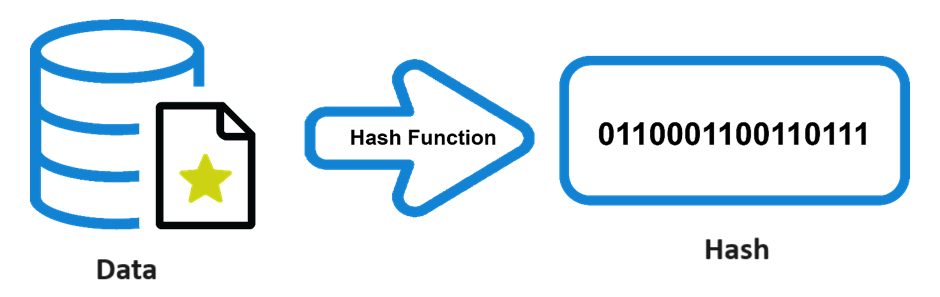
- Before signing a document, the data that needs to be signed (such as a file or a message) is prepared. The entire content of the data is processed through a hash function which produces fixed-size hash values often referred to as the hash digest or simply the hash. This value is a condensed representation of the original data.
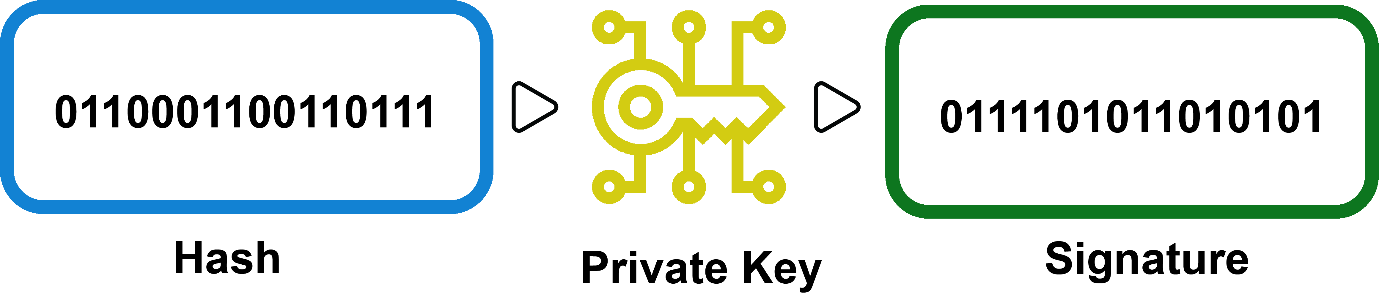
- The hash value is then encrypted using the private key of the signer. This process is typically done through asymmetric cryptography, where the private key is used for encryption, and the corresponding public key is used for verification.
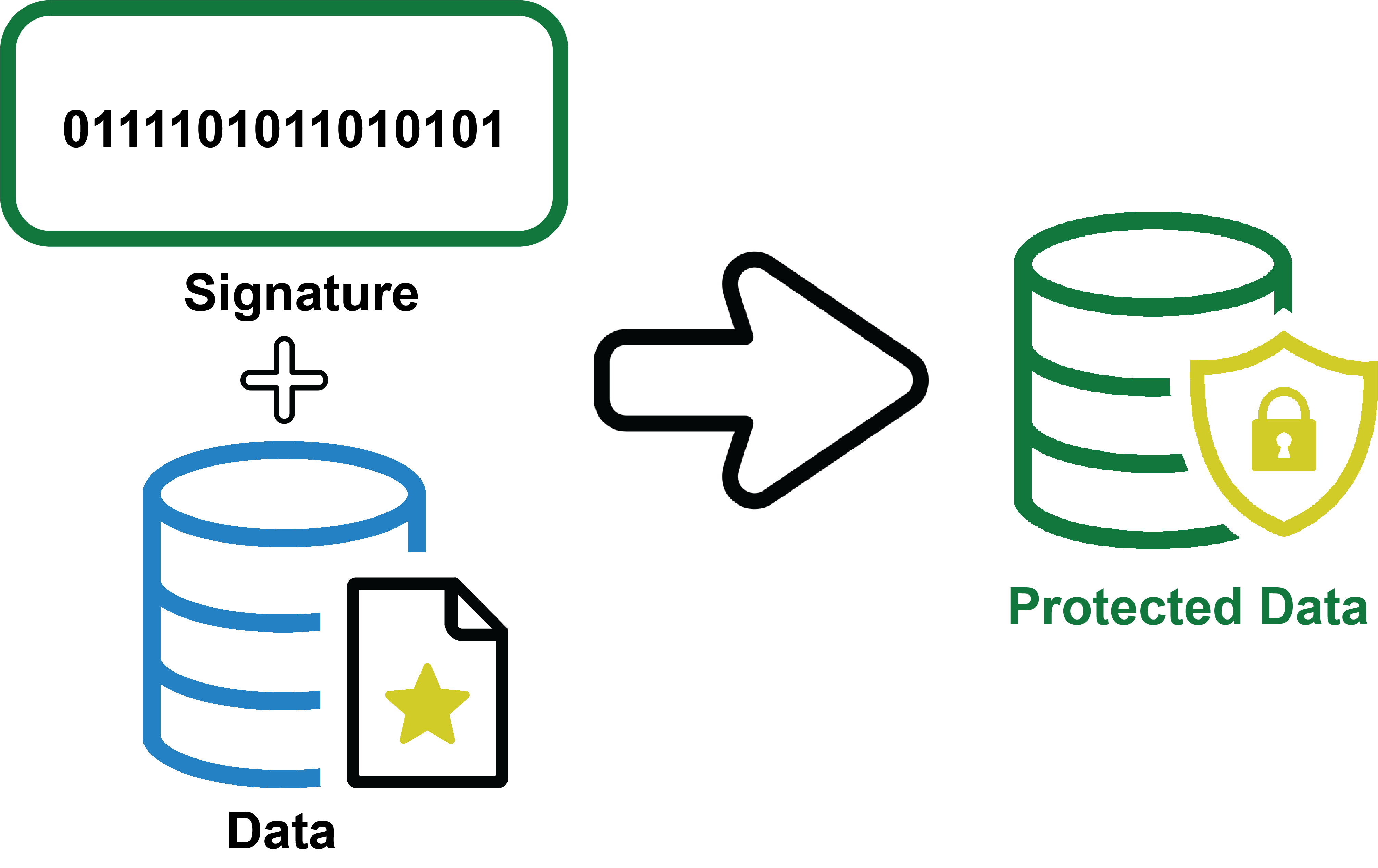
- The resulting encrypted hash value, known as the digital signature, is combined with the signer’s public key. This combination forms the digital signature block, which is then attached to the original data.
- The signed data, comprising the original content and the attached digital signature, is sent to the recipient or made publicly available.
Verifying Digital Signature
To verify the digital signature, the recipient retrieves the attached digital signature block, which includes the encrypted hash value and the signer’s public key. The recipient uses the public key to decrypt the encrypted hash value, revealing the original hash value. The recipient independently calculates the hash value of the received data using the same hash function that was used during the signing process.
If the calculated hash value matches the decrypted hash value obtained from the digital signature, it indicates that the data has not been altered since the signature was applied.
Types of Digital Signatures
There are several types of digital signatures. Here are two of the common types:
PAdES (PDF Advanced Electronic Signatures):
- Specifically designed for electronic signatures in PDF documents.
- Compliant with PDF and ISO standards.
- Ensures the integrity and authenticity of the signed PDF documents.
HMAC (Hash-based Message Authentication Code):
- Combines a cryptographic hash function with a secret key.
- Often used for data integrity and authentication in various protocols.
- Relies on the security of the underlying hash function.
Which countries or regions legally recognize the use of digital signatures?
Digital signatures are recognized and legally valid in many jurisdictions around the world. The acceptance and legal status of digital signatures can vary, and it’s important to consider specific laws and regulations in each jurisdiction. The United States has the Electronic Signatures in Global and National Commerce Act (ESIGN) and the Uniform Electronic Transactions Act (UETA), which provide legal recognition to electronic signatures. The eIDAS Regulation (Electronic Identification and Trust Services) is applicable in the European Union. It establishes a legal framework for electronic signatures and other electronic identification methods.
Conclusion
Together, digital signatures and digital certificates create a secure and trusted environment for document handling. They are widely used in various fields, including legal agreements, financial transactions, and secure communications, to ensure the authenticity, integrity, and non-repudiation of digital documents. We hope that you have found this blog post to be helpful. If you want to quickly get started with digital signatures in the eViewer HTML5, you can check out our interactive demo.